How To Enable Ssl In Windows 10
This topic describes how to enable HTTP on Windows for all the BMC Deject Lifecycle Management components. It also provides detailed configuration steps to make the secured communication between the components.
Note
Mixing protocols in a BMC Cloud Lifecycle Environment deployment isnot supported. All of the BMC Deject Lifecycle Environment components (for example, AR Organisation Mid Tier, Platform Managing director, Quick Start, and the My Cloud Services panel) must exist in HTTP fashionor in HTTPS mode.
Tip
Re-create and paste the SSL commands into a text editor like Notepad++ or TextPad, strip out the line breaks, and modify the syntax for your surroundings.
CLM applications that support HTTPS on SSL during installation
The post-obit table lists the CLM applications that support HTTPS on SSL during installation:
| Product | Self-sign certificate? | Notes on integration path |
|---|---|---|
| Platform Manager | Yes | Import the Platform Manager cacerts file into the JRE of the following products:
|
| Cloud Portal Spider web Application | Yes | Import Cocky-Checker certificate to brandish the Dashboard Data. |
| CLM Self-Check Monitor | Yes | |
| BMC Server Automation (BBSA) | Yes | |
| BMC Network Automation (BBNA) | Aye | |
| Atrium Core Web Services | Aye | Default HTTPS port is 7776. If you use port 7776, update information in the BMC Network Automation console. |
| Mid Tier | No | |
| BMC Atrium Orchestrator | No |
Before you brainstorm
- Have a snapshot of your VMs or support your servers. This precaution is necessary if you make a fault and need to roll back your changes!
- When importing certificates, keypairs, or keystores, utilize the JRE embedded with the production or the latest version of JRE/Java installed on your host.
- If yous are using a Google Chrome browser and run into the weak ephemeral Diffie-Hellman key mistake, run into KA428034 for a helpful workaround. To review this workaround in context, see To configure AMREPO to work with SSL.
Note
BMC tests SSL with OpenSSL generated certificates, equally shown in this topic. But many customers in their production environments have root certificates issued by trusted document authorities (CA), for example, Verisign.
To create a Root CA document using OpenSSL
Note
Yous need the RootCA.key when you configure the Mid Tier, Atrium Core Spider web Services, and BMC Atrium Orchestrator with HTTPS on SSL.
- Download and install 64-fleck OpenSSL1.0 on its own host.
For example, download OpenSSL from the Shining Light Productions website. There are multiple OpenSSL versions available. Brand sure that you install an OpenSSL version that includes the openSSL.cfg file. - CreateKeys,Certificates, andCSR folders.
These categories are for placing keys, certificates files, and then on. - Open up a control prompt and navigate to the OpenSSL folder.
-
Generate the cardinal pair for root CA.
Store this key pair in theC:\Keys\RootCA.key file.C:\OpenSSL-Win64\bin>openssl genrsa -out C:\Keys\RootCA.key 2048 Loading 'screen' into random state - done Generating RSA private key, 2048 bit long modulus ...............++++++ ....................................................++++++ e is 65537 (0x10001) -
Generate a self signed document for CA.
This CA certificate is used across all cloud products every bit a common document. Shop the certificate in theRootCA.crt file.-
Enter the following command:
C:\OpenSSL-Win64\bin>openssl req -config C:\OpenSSL-Win64\bin\openSSL.cfg -new -x509 -days 365 -key C:\Keys\RootCA.key -out C:\Certificates\RootCA.crt -
Create a Distinguished Name (DN)..
Make sure that y'all enter all required data. Many fields contain defaults. Some settings y'all tin can leave bare. If yous enter a period, the field volition be left blank.Country Proper noun (2 letter code) [AU]:Us State or Province Proper name (full name) [Some-Land]:California Locality Proper name (eg, metropolis) []:San Jose Organization Proper name (eg, company) [Cyberspace Widgits Pty Ltd]:BMC Software Organizational Unit of measurement Name (eg, department) []:IDD Common Name (due east.g. server FQDN or YOUR name) []:clm-aus-011538.bmc.com Email Address []:jstamps@bmc.com - PrintingEnter to create the certificate.
-
To import self-signed certificates for new four.6 installations
When you are performing new installations, you must import SSL certificates for Small or Medium deployments.
Note
For Compact deployment, y'all do non need to import the cacerts file since all the product components are on a single host.
Note
In version 4.6, only Compact, Small, and Medium deployments are supported.
The post-obit CLM productsalready have HTTPS/SSL enabled past default:
- Platform Manager
- Cocky-Check Monitor
- Deject Portal Web Application
- BMC Network Automation
- BMC Server Automation
- BMC Capacity Optimization (if you assigned HTTPS/8443 over SSL during installation)
If you installed Platform Manager with the installer planner on HTTPS/SSL with Modest or Medium deployments, you lot withal must import thecacerts file from the Platform Director into the JRE on the following products:
- Mid Tier
- Cloud Portal Spider web Application
- CLM Self-Bank check Monitor
- Cloud Portal and Database AR System server
-
Atrium Orchestrator
Notation
Before you import the cacerts file, BAO Access Manager must already be configured to apply HTTPS/8443 over SSL and BAO CDP must be configured to utilise HTTPS/9443 over SSL. For more than information, see To configure BMC Atrium Orchestrator with SSL.
-
Copy thecacerts file on the Platform Manager to the product host.
For case, re-create thecacerts file from the installed JVM on Platform Manager to theC:\TEMP folder.Note
The cacerts file installed with the Platform Manager from the installed Oracle 64-chip 1.8 JVM is located by default at C:\Program Files\BMC Software\BMCCloudLifeCycleManagement\JVM_1.8.0_60\lib\security for version four.6.
- Open a command window on the product host.
- Change directories to the JRE version 8bin directory (for instance,C:\Program Files\BMC Software\CloudPortalWebApplication\jre\bin)
-
Import the keystore (cacerts) document in the awardingcacerts.
Make sure that yous understand which JRE your application used during installation. This case imports the keystore certificate into thecacerts of an external JRE used.keyTool -importkeystore -srckeystore "C:\TEMP\cacerts" -destkeystore "C:\Program Files\Java\jre7\lib\security\cacerts" -srcstoretype JKS -deststoretype JKS -srcstorepass changeit -deststorepass changeit -nopromptHowever, this example imports the keystore certificate into thecacerts of thebundledJRE used by the Cloud Portal Web Awarding (clmui).
keytool -importkeystore -srckeystore "C:\TEMP\cacerts" -destkeystore "C:\Programme Files\BMC Software\CloudPortalWebApplication\jre\lib\security\cacerts" -srcstoretype JKS -deststoretype JKS -srcstorepass changeit -deststorepass changeit -noprompt -
To monitor Dashboard Data, import the CLM Self-Bank check Monitor certificate (selfcheckSslCertificate.cert) with the JRE used past the Cloud Portal Web Application (whether installed on the Platform Manager or on a split up host) during installation.
The default location ofselfcheckSslCertificate.cert isC:\Programme Files\BMC Software\SelfChecker\selfchecker\Certificates. -
Restart the application service.
For instance, restart the BMC CSM Portal service. -
Flush the browser enshroud.
- Clear the Mid Tier Plugins Cache.
- Log on to the application, add and confirm the site exception, and and then on.
- On the Mid Tier host, createKeys,Certificates, andCSR folders.
- Stop the Mid Tier Tomcat server.
- Open up a command prompt and navigate to the JRE binder.
-
Create a keypair using thekeytool utility.
If the Mid Tier is behind a load balancer, employ CN as the load balancer proper name. Just here it is vw-aus-clnidd03.C:\Program Files\Java\jre7\bin>keytool.exe -genkey -alias tomcat -keyalg RSA -keysize 2048 -keypass "changeit" -storepass "changeit" -keystore C:\Keys\keystore.jks -
At the prompts, enter the required information to create the keypair, and then press Enter.
C:\Programme Files\Java\jre7\bin>keytool.exe -genkey -alias tomcat -keyalg RSA -keysize 2048 -keypass "changeit" -storepass "changeit" -keystore C:\Keys\keystore.jks What is your first and last proper noun? [Unknown]: vw-aus-clnidd03 What is the name of your organizational unit of measurement? [Unknown]: IDD What is the name of your organization? [Unknown]: BMC What is the name of your Metropolis or Locality? [Unknown]: SAN JOSE What is the proper noun of your State or Province? [Unknown]: CA What is the two-letter of the alphabet country code for this unit? [Unknown]: The states Is CN=vw-aus-clnidd03, OU=IDD, O=BMC, L=SAN JOSE, ST=CA, C=US correct? [no]: yep -
Create the Certificate Signing Asking (CSR) from Mid Tier master to retrieve the certificate from CA (i.e. CLM).
C:\Program Files\Java\jre7\bin>keytool.exe -certreq -keyalg RSA -alias tomcat -file C:\CSR\mt.csr -keystore C:\Keys\keystore.jks Enter keystore countersign:At the prompt, enter changeit equally the password.
-
Re-create the mt.csr file to the CSR binder where OpenSSL is installed so that you can generate a document, and and so run the post-obit command on the OpenSSL computer:
C:\OpenSSL-Win64\bin>openssl x509 -req -days 365 -in C:\CSR\mt.csr -CA C:\Certificates\RootCA.crt -CAkey C:\Keys\RootCA.primal -set_serial 01 -out C:\Certificates\mt_server.crt Loading 'screen' into random state - done Signature ok discipline=/C=U.s.a./ST=CA/Fifty=SAN JOSE/O=BMC/OU=IDD/CN=vw-aus-clnidd03 Getting CA Individual Key -
After the certificate is generated (mt_server.crt) in the Certificates binder, copy mt_server.crt and RootCA.crt to the Mid Tier main and secondary computers into their Certificates folder.
-
On the Mid Tier chief and secondary computers, import the Root CA document:
C:\Program Files\Java\jre7\bin>keytool.exe -import -alias root -keystore C:\Keys\keystore.jks -trustcacerts -file C:\Certificates\RootCA.crt Enter keystore countersign: Owner: EMAILADDRESS=jstamps@bmc.com, CN=JOHN, OU=IDD, O=BMC, Fifty=SJ, ST=CA, C=US Issuer: EMAILADDRESS=jstamps@bmc.com, CN=JOHN, OU=IDD, O=BMC, L=SJ, ST=CA, C=United states of america ... Trust this certificate? [no]: aye Certificate was added to keystore C:\Program Files\Java\jre7\bin>-
At the prompt, enterchangeitequally the password.
- When yous run into the Trust this certificate prompt, enter yes.
Your certificate is added to the keystore.
-
-
Import the mt_server.crt certificate:
C:\Program Files\Java\jre7\bin>keytool.exe -import -alias tomcat -keystore C:\Keys\keystore.jks -trustcacerts -file C:\Certificates\mt_server.crt Enter keystore password: Certificate reply was installed in keystoreAt the prompt, enterchangeitas the password. Your certificate reply is installed in the keystore.
- Open the server.xml file (in Windows, the default location is C:\Program Files\Apache Software Foundation\Tomcat6.0\conf\server.xml) in a text editor and uncomment the SSL related sections.
-
Search for the following text and uncomment out the
Connector portsection:
<!-- Define a SSL HTTP/1.1 Connector on port 8443 This connector uses the JSSE configuration, when using APR, the connector should exist using the OpenSSL style configuration described in the April documentation --> <!-- <Connector port="8443" protocol="HTTP/1.1" SSLEnabled="true" maxThreads="150" scheme="https" secure="true" clientAuth="false" sslProtocol="TLS" /> --> -
Modify the
Connector portinformation as follows:
<Connector port="9443" protocol="HTTP/1.i" SSLEnabled="true" maxThreads="150" scheme="https" secure="truthful" clientAuth="simulated" sslProtocol="TLS" keystoreFile="C:\Keys\keystore.jks" keystorePass="<passwordMustEqualYourKeystorePassword>" />Hither you modify the connector port to 9443 and add the keyStore file location and keystore countersign.
Note
If yous do not add the right keystore countersign, the Tomcat server does non starting time properly.
-
Save the server.xml .
-
- Start the Tomcat server.
- Verify your changes to the Mid Tier or Mid Tier Load Balancer by accessing the following URL:
https://midTier:9443/arsys (where 9443 is SSL port)
https://loadBalancer:9443/arsys - Add together and confirm any security restrictions in your browser.
- When yous access the Mid Tier the get-go time, review the document details.
- Review the General tab and verify who the certificate is issued to and who information technology was issued by.
- Click the Details tab and, review the certificate path or hierarchy.
- Proceed logging on to the Cloud Portal and Database AR System server.
To integrate the Mid Tier with Platform Manager
- Open up the CMF:PluginConfiguration form in Search mode in the Cloud Portal and Database AR Organisation server.
- Search for the CallBackURIrecord.
- Edit the CallBackURIfrom http to https.
- Edit the port to 9443.
- Salve the record.
-
Copy the RootCA.crt certificate from the Mid Tier server to the Platform Manager server (for example, to a Certificates folder).
-
Open up a command window and change directories to C:\Program Files\BMC Software\BMCCloudLifeCycleManagement\JVM_1.vii.0_55\bin (by default).
-
Back upwards the ..\JVM_1.7.0_55\lib\security\ cacerts file.
-
Import the certificate:
keytool.exe -import -alias root -keystore "C:\Program Files\BMC Software\BMCCloudLifeCycleManagement \JVM_1.7.0_55\lib\security\cacerts" -trustcacerts -file "C:\Certificates\RootCA.crt" Enter keystore countersign: Re-enter new password: ... Trust this document? [no]: aye Certificate was added to keystore - At the prompt, enterchangeitas the password.
- When you see theTrust this document prompt, enteryes.
Your certificate is added to the keystore. - Restart the services in the following order – showtime BMC CSM on Platform Manager and second the Cloud Portal and Database AR System server.
To configure Atrium Web Services SSL
The post-obit instructions apply but to Small or Medium deployments.
Note
In Compact Deployment, Atrium Spider web Services are not available as a separate component. Instead, they are installed as part of the Mid Tier. As a result, y'all do non need to configure SSL separately for Compact Deployment.
- On the master Atrium Cadre Web Services Registry host, createKeys,Certificates, andCSR folders.
- Finish the Atrium Tomcat server.
- Open up a control prompt and navigate to the JRE folder.
-
Create a keypair using thekeytool utility.
If the Atrium Spider web Services are behind a load balancer, you tin utilise CN as the load-balancer name. Simply here it is vw-aus-clnidd01.C:\Program Files\Java\jre7\bin>keytool.exe -genkey -alias tomcat -keyalg RSA -keysize 2048 -keypass "changeit" -storepass "changeit" -keystore C:\Keys\keystore.jks -
At the prompts, enter the required data to create the keypair, and so pressEnter.
keytool.exe -genkey -alias tomcat -keyalg RSA -keysize 2048 -keypass "changeit" -storepass "changeit" -keystore C:\Keys\keystore.jks What is your get-go and last name? [Unknown]: vw-aus-clnidd01 What is the proper name of your organizational unit? [Unknown]: IDD What is the proper noun of your arrangement? [Unknown]: BMC What is the name of your Metropolis or Locality? [Unknown]: SAN JOSE What is the proper name of your State or Province? [Unknown]: CA What is the two-alphabetic character country code for this unit? [Unknown]: US Is CN=vw-aus-clnidd01, OU=IDD, O=BMC, 50=SAN JOSE, ST=CA, C=United states of america correct? [no]: yes -
Create the Document Signing Request (CSR) from Atrium Web Services primary to retrieve the certificate from CA (that is, CLM).
C:\Programme Files\Java\jre7\bin>keytool.exe -certreq -keyalg RSA -alias tomcat -file C:\CSR\aws.csr -keystore C:\Keys\keystore.jks Enter keystore password:At the prompt, enter changeit as the password.
-
Copy the aws.csr file to the CSR folder where OpenSSL is installed so that you can generate a document (aws_server.crt), then run the following control on the OpenSSL calculator:
C:\OpenSSL-Win64\bin>openssl x509 -req -days 365 -in C:\CSR\aws.csr -CA C:\Certificates\RootCA.crt -CAkey C:\Keys\RootCA.key -set_serial 01 -out C:\Certificates\aws_server.crt Loading 'screen' into random state - done Signature ok subject=/C=US/ST=CA/L=SAN JOSE/O=BMC/OU=IDD/CN=vw-aus-clnidd01 Getting CA Private Key -
After the certificate is generated (aws_server.crt) in theCertificates folder, copyaws_server.crt andRootCA.crt to the AWS primary and secondary hosts into theirCertificates binder.
-
On the AWS primary and secondary hosts, import the Root CA certificate:
C:\Programme Files\Java\jre7\bin>keytool.exe -import -allonym root -keystore C:\Keys\keystore.jks -trustcacerts -file C:\Certificates\RootCA.crt Enter keystore password: Owner: EMAILADDRESS=jstamps@bmc.com, CN=vw-aus-clmidd05.bmc.com, OU=IDD, O=BMC, L=SAN JOSE, ST=CA, C=US ... Trust this certificate? [no]: yep Certificate was added to keystore-
At the prompt, enter changeit as the password.
-
When you see the Trust this certificate prompt, enter yes .
Your certificate is added to the keystore.
-
-
Import the aws_server.crt certificate:
C:\Program Files\Java\jre7\bin>keytool.exe -import -alias tomcat -keystore C:\Keys\keystore.jks -trustcacerts -file C:\Certificates\aws_server.crt Enter keystore password: Certificate reply was installed in keystoreYour certificate respond is installed in the keystore.
- Open the server.xml file (in Windows, the default location isC:\Programme Files\BMC Software\Atrium Web Registry\shared\tomcat\conf\server.xml) in a text editor and uncomment the SSL related sections.
-
Search for the following text and uncomment out the
Connector portdepartment:
<!-- Define a SSL HTTP/i.i Connector on port 8443 This connector uses the JSSE configuration, when using Apr, the connector should exist using the OpenSSL mode configuration described in the April documentation --> <!-- <Connector port="8443" protocol="HTTP/one.1" SSLEnabled="truthful" maxThreads="150" scheme="https" secure="true" clientAuth="false" sslProtocol="TLS" /> --> -
Modify the
Connector portinformation as follows:
<Connector port="9443" protocol="HTTP/i.ane" SSLEnabled="true" maxThreads="150" scheme="https" secure="true" clientAuth="fake" sslProtocol="TLS" keystoreFile="C:\Keys\keystore.jks" />Here you change the connector port to 9443 and add the keyStore file location.
-
Save theserver.xml .
-
- Commencement the AWS Tomcat server.
- Verify your changes to the AWS or AWS Load Balancer past accessing the following URL:
https://<AWS>:9443 (where 9443 is SSL port)
https://<LoadBalancer>:9443 -
Add together and confirm any security restrictions in your browser.
- When you lot access AWS UDDI the outset fourth dimension, review the certificate details.
- Review who the document is issued to (for case, vw-aus-clnidd01 ) and who the certificate was issued by (for case, bmc.com ).
- Review the certificate path or hierarchy.
To integrate Atrium Web Services with BMC Network Automation
The following instructions employ simply to Small or Medium deployments.
Note
In Compact Deployment, Atrium Web Services are not bachelor equally a separate component. Instead, they are installed every bit part of the Mid Tier. As a effect, you lot do not need to configure SSL separately for Compact Deployment.
-
Log on to the Mid Tier to access the Cloud Portal and Database AR System server.
You tin can use https://<MidTier>:9443/arsys to admission the Cloud Portal and Database AR System server.Notation
If yous are running a dual AR Organisation server environment, modify the default web path for the Enterprise-AR and Deject-AR servers.
- Open the Server Information form for the Cloud Portal and Database AR System server.
- Click the Advanced tab, and alter the URL in the Default Web Path field with the updated https and port (for example, 9443).
For instance, you might enter https://vw-san-clmidd:9443/arsys/. - Restart the Cloud Portal and Database AR System server.
- Log on to BMC Network Automation.
For example, go to https://bnaServer:11443/bca-networks - Click the Admin tab, and navigate to System Admin > Organization Parameters.
- In theEnable CMDB Integration section, change the Web Service Endpoint URL field with the updated https and port 9443 URL (for instance, https://bnaServer:9443/cmdbws/server/cmdbws.wsdl ).
- Click Salvage.
The BMC Network Automation panel verifies your changes. - When you finish, verify that physical location is accessed past BMC Network Automation during POD creation through the Atrium Web Services.
If you have successfully integrated Atrium Spider web service and BNA SSL communication, go to BMC Network Automation and effort to create a POD. The physical location created in the AR System server should exist visible in the listing during POD creation.
To configure SSL with BMC Server Automation
Warning
If you installed BMC Server Automation with the default settings, HTTPS on SSL is already enabled. Practice not complete these steps if SSL is already enabled on the host. Otherwise, y'all run the risk of accidentally breaking functionality that is already working properly.
For more data onusing a CA-issued document or certificate chain rather than the default self-signed certificate, seeSecuring communication with CA certificates in the BMC Server Automation documentation.
- On the BMC Server Automation host, createKeys,Certificates, andCSR folders.
- Stop the BladeLogic Application Server.
-
Back up the bladelogic.keystore file, located at C:\Program Files\BMC Software\BladeLogic\appserver\br\deploymentsorC:\Program Files\BMC Software\BladeLogic\NSH\br\deployments and then delete the original.
- Open a control prompt and navigate to the BladeLogic JRE folder (for case, C:\Plan Files\BMC Software\BladeLogic\NSH\jre\bin).
-
On the BMC Server Automation main host, create a keypair using thekeytool utility.
If BMC Server Automation is backside a load balancer, you tin can utiliseCN as the load-balancer name.Note
In the keytool syntax, use the password yous created when you installed BMC Server Automation, not changeit.
keytool.exe -genkey -allonym blade -keyalg RSA -keysize 2048 -keypass "<countersign>" -storepass "<countersign>" -keystore "C:\Program Files\BMC Software\BladeLogic\NSH\br\ deployments\_template\bladelogic.keystore" What is your get-go and last name?What is your first and last proper noun? [Unknown]: JOHN STAMPS What is the name of your organizational unit? [Unknown]: IDD What is the name of your organization? [Unknown]: BMC What is the name of your City or Locality? [Unknown]: SAN JOSE What is the name of your State or Province? [Unknown]: CA What is the ii-letter of the alphabet country code for this unit of measurement? [Unknown]: U.s.a. Is CN=JOHN STAMPS, OU=IDD, O=BMC, Fifty=SAN JOSE, ST=CA, C=US right? [no]: yes - At the prompts, enter the required information to create the keypair, and and then pressEnter.
-
Create the Document Signing Request (CSR) from BMC Server Automation primary to retrieve the document from CA (that is, CLM).
keytool.exe -certreq -keyalg RSA -alias blade -file C:\CSR\blade.csr -keystore "C:\Plan Files\BMC Software\ BladeLogic\NSH\br\deployments\_template\bladelogic.keystore" Enter keystore password:
At the prompt, enter the BMC Server Automation password, not changeit. -
Copy the blade.csr file to the CSR folder where OpenSSL is installed and so that yous can generate a certificate (blade.crt), and and so run the following command on the OpenSSL computer:
C:\OpenSSL-Win64\bin>openssl x509 -req -days 365 -in C:\CSR\blade.csr -CA C:\Certificates\RootCA.crt -CAkey C:\Keys\RootCA.key -set_serial 01 -out C:\Certificates\blade.crt Loading 'screen' into random land - washed Signature ok field of study=/C=U.s.a./ST=CA/L=SAN JOSE/O=BMC/OU=IDD/CN=JOHN STAMPS Getting CA Private Central -
After the certificate is generated (blade.crt) in theCertificates binder, copy bract.crt andRootCA.crt to the BMC Server Automation primary host into itsCertificates folder.
-
On the BMC Server Automation chief host, import the Root CA certificate:
keytool.exe -import -alias blade -keystore "C:\Program Files\BMC Software\BladeLogic\NSH\ br\deployments\_template\bladelogic.keystore" -trustcacerts -file C:\Certificates\RootCA.crt Enter keystore password: Owner: EMAILADDRESS=jstamps@bmc.com, CN=JOHN, OU=IDD, O=BMC, L=SJ, ST=CA, C=United states Issuer: EMAILADDRESS=jstamps@bmc.com, CN=JOHN, OU=IDD, O=BMC, 50=SJ, ST=CA, C=The states ... Trust this document? [no]: yeah Certificate was added to keystore- At the prompt, enter the BMC Server Automation password, not changeit.
-
When yous encounter theTrust this document prompt, enteraye.
Your document is added to the keystore.
-
Import the bract.crt certificate:
C:\Programme Files\BMC Software\BladeLogic\NSH\jre\bin>keytool.exe -import -alias blade -keystore "C:\Program Files\BMC Software\BladeLogic\NSH\ br\deployments\_template\bladelogic.keystore" -trustcacerts -file C:\Certificates\blade.crt Enter keystore password: Certificate reply was installed in keystore
Your certificate respond is installed in the keystore. - Re-create thebladelogic.keystore file yous merely created from the _template folder to each of thedeployments server folders.
- Start theBladeLogic Application Server.
- Verify your changes to the BMC Server Automation URL by accessing the following link:
https://<BladeLogic>:10843 (where 10843 is the SSL port)
- When you access BMC Server Automation URL the first time, review the document details.
- Log on to theBladeLogic Application Server.through BMC Server Automation Console.
In the login screen, click Options > Certificates > View to view the certificate. This screen displays the certificate details like issued to clm-hou-bbsa and Issued past CA (for example, CLM). - For BMC Server Automation secondary, follows the relevant steps (typicallyone > 2 > three > 12 > 13 >14 >15 >16 >17 in order).
To configure SSL with BMC Server Automation and Platform Manager
- On the Platform Manager host, open theproviders.json file.
-
Change the protocol and the SSL port in the providers.jsonfile for theBBSA_SERVER_PORT attribute value.
For example:
"name" : "BBSA_SERVER_PORT" }, "attributeValue" : "10843", "description" : "BBSA Webservices Port", "guid" : "1a0e98f9-905e-4117-99dd-759f7ad41b71", "name" : "BBSA_SERVER_PORT" }, { "cloudClass" : "com.bmc.cloud.model.beans.AccessAttributeValue", "accessAttribute" : { "cloudClass" : "com.bmc.cloud.model.beans.AccessAttribute", "datatype" : "STRING", "clarification" : "BBSA Server Protocol", "guid" : "3bf2db7a-af7e-4bc7-8674-63c6df997a75", "isOptional" : simulated, "isPassword" : false, "modifiableWithoutRestart" : false, "proper noun" : "BBSA_SERVER_PROTOCOL" }, "attributeValue" : "https", "description" : "BBSA Server Protocol", - Save your changes and restart the Platform Director.
To configure BMC Network Automation with SSL
Warning
If y'all installed BMC Network Automation with the default settings, HTTPS on SSL is already enabled. Do non complete these steps if SSL is already enabled on the host. Otherwise, you lot run the risk of accidentally breaking functionality that is already working properly.
Notation
The BMC Network Automation CLI might not use the default JVM arranged with BNA (for instance, C:\Program Files\BMC Software\BCA-Networks\java\bin). In this case, you must import the root (and whatsoever intermediate) certificates into the keystore of the native JVM of the Bone (in Windows, for example,C:\Program Files\Jave\jre7\lib\security\cacert).
- On the BMC Network Automation host, createKeys,Certificates, andCSR folders.
- Terminate the BCA-Networks Web Server.
- Dorsum up the .keystore file (past default, located at C:\BCA-Networks-Data) and then delete the original.
- On the master BMC Network Automation host, open a command prompt and navigate to the BCA-Network JRE binder (for example,C:\Program Files\BMC Software\BCA-Networks\java\bin).
-
Create a keypair using thekeytool utility.
If BMC Network Automation is behind a load balancer, you can utiliseCN equally the load-balancer name. Use the following syntax so that keytool works properly:C:\Program Files\BMC Software\BCA-Networks\java\bin>keytool.exe -genkey -alias clm-bna -keyalg RSA -keysize 2048 -keypass "changeit" -storepass "changeit" -keystore "C:\BCA-Networks-Information\.keystore" What is your first and last name? [Unknown]: JOHN STAMPS What is the proper noun of your organizational unit? [Unknown]: IDD What is the name of your organization? [Unknown]: BMC What is the proper noun of your City or Locality? [Unknown]: SAN JOSE What is the name of your State or Province? [Unknown]: CA What is the two-letter state code for this unit of measurement? [Unknown]: Us Is CN=JOHN STAMPS, OU=IDD, O=BMC, L=SAN JOSE, ST=CA, C=United states correct? [no]: yeah - At the prompts, enter the required information to create the keypair, and then pressEnter.
-
Create the Certificate Signing Request (CSR) from BMC Network Automation primary to retrieve the certificate from CA (that is, CLM).
keytool.exe -certreq -keyalg RSA -allonym clm-bna -file C:\CSR\clm-bna.csr -keystore "C:\BCA-Networks-Data\.keystore" Enter keystore password:
At the prompt, enter changeit as the countersign. -
Copy the clm-bna.csr file to the CSR folder where OpenSSL is installed then that you can generate a certificate (clm-bna.crt), so run the following control on the OpenSSL computer:
C:\OpenSSL-Win64\bin>openssl>openssl x509 -req -days 365 -in C:\CSR\clm-bna.csr -CA C:\Certificates\RootCA.crt -CAkey C:\Keys\RootCA.key -set_serial 04 -out C:\Certificates\clm-bna.crt Loading 'screen' into random state - washed Signature ok subject=/C=Us/ST=CA/L=SAN JOSE/O=BMC/OU=IDD/CN=clm-bna Getting CA Individual Primal -
After the certificate is generated (clm-bna .crt) in theCertificates folder, copyclm-bna .crt andRootCA.crt to the BMC Network Automation main and secondary hosts into theirCertificates folder.
-
On the BMC Network Automation primary and secondary computers, import the first Root CA certificate into the C:\BCA-Networks-Data\.keystore file that we generated:
C:\Program Files\BMC Software\BladeLogic\NSH\jre\bin>keytool.exe -import -allonym root -keystore "C:\BCA-Networks-Data\.keystore" -trustcacerts -file C:\Certificates\RootCA.crt Owner: EMAILADDRESS=jstamps@bmc.com, CN=bmc.com, OU=IDD, O=BMC, Fifty=San Jose, ST=CA, C=US ... Trust this certificate? [no]: aye Document was added to keystore- At the prompt, enterchangeitas the password.
-
When you see theTrust this certificate prompt, enteraye.
Your certificate is added to the keystore. - If you have a secondary BMC Network Automation reckoner, import only the RootCA certificate in the java\cacerts file.
-
ImportRoot CA into the C:\Programme Files\BMC Software\BCA-Networks\java\lib\security\cacerts file:
C:\Program Files\BMC Software\BCA-Networks\java\bin>keytool.exe -import -allonym root -keystore "C:\Program Files\BMC Software\BCA-Networks\java\lib\security\cacerts" -trustcacerts -file C:\certificates\RootCA.crt Enter keystore countersign: Owner: EMAILADDRESS=jstamps@bmc.com, CN=bmc.com, OU=IDD, O=BMC, L=San Jose, ST=CA, C=US ... Trust this document? [no]: yeah Certificate was added to keystore -
Import theblm-bna.crt document:
C:\Program Files\BMC Software\BCA-Networks\java\bin>keytool.exe -import -alias clm-bna -keystore C:\BCA-Networks-Data\.keystore -trustcacerts -file C:\Certificates\clm-bna.crt Enter keystore password: Certificate reply was installed in keystore
Your certificate reply is installed in the keystore. -
Generate the encryption cord for changeit.
-
Open up the BNA maintenance utility (by default, installed in C:\Program Files\BMC Software\BCA-Networks\utility).
-
Click the Encrypt tab.
-
Enter and ostend the changeit password.
-
Click Encrypt to generate the encryption string for changeit.
-
Use the generated string for the keystorePassword parameter in the server.xmlfile (by default, located at C:\Program Files\BMC Software\BCA-Networks\tomcat\conf ).
-
-
Starting time theBCA-Networks Spider web Server .
- Verify the BNA link by accessing https://<BNA-LB>:443 where 443 is SSL port.
- If you have a load balancer, failover the BNA service and verify that yous can able to access the link with Cluster name and with the aforementioned certificate it displays.
-
When yous access the BMC Network Automation URL the showtime time, review the document details, and so on.
Note
No integration level changes are required for BMC Network Automation. In the providers.json file on the Platform Managing director host, the BNA department is already populated with the https protocol and SSL port. This SSL port should be same on which you configured BMC Network Automation.
To configure Platform Managing director from HTTPS to HTTP with a Self-Signed Certificate
Apply the post-obit steps to configure HTTPS to HTTP using a Cocky-Signed Document. If you are running HA, you lot but need to run the following commands on the primary host. SSL-level certification is not required on the secondary HA host.
- Make sure the CSM service is running on the primary Platform Manager host.
- On the principal Platform Manager host, createKeys,Certificates, andCSR folders.
- Back upward thekeystore file (by default, located atC:\Program Files\BMC Software\BMCCloudLifeCycleManagement\Platform_Manager\security).
- Open up a command prompt and navigate to the JRE binder (for instance,C:\Program Files\java\jre7\bin).
-
Create a keypair using thekeytool utility and store information technology atC:\Programme Files\BMC Software\BMCCloudLifeCycleManagement\Platform_Manager\security.
keytool.exe -genkey -allonym PM -keyalg RSA -keysize 1024 -keypass "changeit" -storepass "changeit" -keystore "C:\Program Files\BMC Software\BMCCloudLifeCycleManagement\ Platform_Manager\security\keystore" What is your first and last name? [Unknown]: clm-hou-pm What is the proper noun of your organizational unit? [Unknown]: IDD What is the name of your organization? [Unknown]: BMC What is the name of your Urban center or Locality? [Unknown]: San Jose What is the name of your State or Province? [Unknown]: CA What is the 2-letter of the alphabet state code for this unit? [Unknown]: United states of america Is CN=clm-hou-pm, OU=IDD, O=BMC, L=San Jose, ST=CA, C=US correct? [no]: yeahAt the prompts, enter the required information to create the keypair, and then pressEnter. For instance, employclm-hou-pmas the cluster proper name.
-
Create the Certificate Signing Request (PM.csr) to retrieve the certificate from Root CA.
keytool.exe -certreq -keyalg RSA -alias PM -file C:\CSR\PM.csr -keystore "C:\Program Files\BMC Software\BMCCloudLifeCycleManagement\ Platform_Manager\security\keystore" Enter keystore password:At the prompt, enterchangeitevery bit the password.
-
Copy thePM .csr file to theCSR folder where OpenSSL is installed then that you tin can generate a certificate (PM.crt), and and so run the following command on the OpenSSL host:
C:\OpenSSL-Win64\bin>openssl x509 -req -days 365 -in C:\CSR\PM.csr -CA C:\Certificates\RootCA.crt -CAkey C:\Keys\RootCA.central -set_serial 01 -out C:\Certificates\pm.crt Loading 'screen' into random state - washed Signature ok subject=/C=US/ST=CA/L=San Jose/O=BMC/OU=IDD/CN=clm-hou-pm Getting CA Private Fundamental -
Afterwards the certificate is generated (PM.crt) in theCertificates folder, copyPM.crt andRootCA.crt to the Platform Managing director primary host into theCertificates folder.
-
On the Platform Director primary host, import the Root CA certificate:
keytool.exe -import -allonym root -keystore "C:\Plan Files\BMC Software\BMCCloudLifeCycleManagement\ Platform_Manager\security\keystore" -trustcacerts -file C:\Certificates\RootCA.crt Enter keystore password: Certificate already exists in system-wide CA keystore nether alias <root> Do you all the same want to add information technology to your own keystore? [no]: yes Certificate was added to keystore- At the prompt, enterchangeitequally the password.
-
If you are prompted that the document already exists, enteraye anyhow;
Your document is added to the keystore.
-
Import the Root CA certificate into the Platform Manager JVMcacerts file.
keytool.exe -import -alias root -keystore "C:\Programme Files\BMC Software\BMCCloudLifeCycleManagement\ JVM_1.6.0_31\lib\security\cacerts" -trustcacerts -file C:\Certificates\RootCA.crt Enter keystore password: Certificate was added to keystore -
Import thePM.crt certificate:
keytool.exe -import -alias PM1 -keystore "C:\Program Files\BMC Software\BMCCloudLifeCycleManagement\ Platform_Manager\security\keystore" -trustcacerts -file C:\Certificates\PM.crt Enter keystore password: Certificate was added to keystore -
Update theconfig.ini file (by default, located atC:\Plan Files\BMC Software\BMCCloudLifeCycleManagement\Platform_Manager\configuration) with the following parameters:
org.osgi.service.http.port=7070 jetty.port=7070 jetty.ssl.password=changeit jetty.ssl.keypassword=changeitMake sure to salvage theconfig.ini file.
-
Update the the configuration in the..\Platform_Manager\csm-bootstrap.properties file with the following changes:
PersistenceNodeProtocol=http NodeProtocol=http NodePort=7070 PersistenceNodePort=7070Brand certain to save thecsm-bootstrap.properties file.
- Update the configuration in the..\Platform_Manager\configuration\cloudservices.json file with the post-obit changes:
-
Fix thesecureJettyaspect value tosimulated and theclarification toUse HTTP.
{ "cloudClass" : "com.bmc.cloud.model.beans.CloudService", "accessValues" : [ { "cloudClass" : "com.bmc.cloud.model.beans.AccessAttributeValue", "accessAttribute" : { "cloudClass" : "com.bmc.cloud.model.beans.AccessAttribute", "datatype" : "Boolean", "description" : "Use HTTP", "guid" : "b15fc770-4119-4cd6-bea6-1efdc5ecc768", "isOptional" : false, "isPassword" : imitation, "length" : 255, "modifiableWithoutRestart" : simulated, "name" : "secureJetty" }, "attributeValue" : "false", "description" : "Use HTTP", "guid" : "2aacb37d-0b0c-48f2-b85f-e010e3705f49", "name" : "secureJetty" } -
Set up the aspect value ofJetty port,CSM Local Port, andCSM Global Registry URLto7070.
Brand sure that y'all also set the localhost aspect value to"localhost:7070".{ "cloudClass" : "com.bmc.deject.model.beans.AccessAttributeValue", "accessAttribute" : { "cloudClass" : "com.bmc.cloud.model.beans.AccessAttribute", "datatype" : "Integer", "description" : "Jetty Port", "guid" : "f1f036cc-7050-4a08-9e00-2a38cedaeef9", "isOptional" : false, "isPassword" : false, "length" : 255, "modifiableWithoutRestart" : simulated, "proper name" : "jettyPort" }, "attributeValue" : "7070", "clarification" : "Jetty Port", "guid" : "e2513a26-1c6c-4fd1-9267-d3ff3d00b94a", "proper name" : "jettyPort" } { "cloudClass" : "com.bmc.cloud.model.beans.AccessAttributeValue", "accessAttribute" : { "cloudClass" : "com.bmc.cloud.model.beans.AccessAttribute", "datatype" : "Integer", "clarification" : "CSM Local Port", "guid" : "9ceda25b-b408-4f38-bf78-26fc8a941ced", "isOptional" : false, "isPassword" : false, "length" : 255, "modifiableWithoutRestart" : false, "name" : "csm.local.port" }, "attributeValue" : "7070", "description" : "CSM Local Port", "guid" : "b86fb3c3-d5c8-46dc-8d7d-5be05a392aff", "name" : "csm.local.port" } },{ "cloudClass" : "com.bmc.cloud.model.beans.CloudService", "accessValues" : [ { "cloudClass" : "com.bmc.deject.model.beans.AccessAttributeValue", "accessAttribute" : { "cloudClass" : "com.bmc.deject.model.beans.AccessAttribute", "datatype" : "String", "description" : "CSM Global Registry URL", "guid" : "5f49c658-e3fb-4ace-95aa-d5c13636a82e", "isOptional" : false, "isPassword" : false, "length" : 255, "modifiableWithoutRestart" : imitation, "name" : "csm.global.url" }, "attributeValue" : "localhost:7070", "description" : "CSM Global Registry URL", "guid" : "45cb9fc3-ac7e-49de-88d4-4d1042c48061", "name" : "csm.global.url" }, { "cloudClass" : "com.bmc.deject.model.beans.AccessAttributeValue", "accessAttribute" : { "cloudClass" : "com.bmc.deject.model.beans.AccessAttribute", "datatype" : "Integer", "description" : "CSM Local Port", "guid" : "9ceda25b-b408-4f38-bf78-26fc8a941ced", "isOptional" : imitation, "isPassword" : simulated, "length" : 255, "modifiableWithoutRestart" : faux, "name" : "csm.local.port" }, "attributeValue" : 7070, "clarification" : "CSM Local Port", "guid" : "80e5622d-4dbc-49de-9ca6-deef7627e7f5", "name" : "csm.local.port" } ], "cloudServiceDefinition" : "/cloudservicedefinition/4bc19dbb-22e5 -4a3d-a294-c3749e2b2947", "cloudServiceDefinitionObject" : { "cloudClass" : "com.bmc.cloud.model.beans.CloudServiceDefinition", "accessAttributes" : [ { "cloudClass" : "com.bmc.cloud.model.beans.AccessAttribute", "datatype" : "String", "description" : "CSM Global Registry URL", "guid" : "5f49c658-e3fb-4ace-95aa-d5c13636a82e", "hasValueObject" : [ { "cloudClass" : "com.bmc.deject.model.beans.AccessAttributeValue", "attributeValue" : "localhost:7070", "guid" : "79c5b890-1b4e-4514-8e28-ddd216551b3c", "proper noun" : "csm.global.url" } ], "isOptional" : false, "isPassword" : false, "length" : 255, "modifiableWithoutRestart" : false, "proper noun" : "csm.global.url" }, { "cloudClass" : "com.bmc.cloud.model.beans.AccessAttribute", "datatype" : "Integer", "description" : "CSM Local Port", "guid" : "9ceda25b-b408-4f38-bf78-26fc8a941ced", "hasValueObject" : [ { "cloudClass" : "com.bmc.deject.model.beans.AccessAttributeValue", "attributeValue" : "7070", "guid" : "de64d5ff-ff11-4e2d-Make sure to save thecloudservices.json file.
-
-
Ready thevalue parameter in the..\Platform_Manager\configuration\PreferenceGroup.json file tohttpand7070.
Note
If y'all programme to have Self-Check Monitor and Cloud Portal Web Application (installed on separate hosts) as well on HTTP, make sure the protocol and port values related to these products are updated accordingly.
{ "cloudClass": "com.bmc.cloud.model.beans.PreferenceGroupNameValuePair", "guid": "98d27d82-44fc-41c8-bde0-007f0fa8fc2f", "name": "clmui base URL", "value": "http://clm-aus-005121/clmui" },{ -
Stop the CSM service and then perform the following actions:
- Dorsum upwards thecache anddata folders in.\Platform_Manager.
- Back up theorg.eclipse.*folders in.\Platform_Manager\configuration.
- Delete thecache,information, andorg.eclipse.*folders.
-
Update the Platform Manager Root URL in theCMF:PluginConfiguration class on the Cloud Portal and Database AR System server tohttp and7070.
-
Start the CSM service.
-
Restart the Cloud Portal and Database AR System service.
-
Use RESTClient to verify the Platform Manager SSL connection by using the SSL link.
To configure Platform Managing director from HTTP to HTTPS with a Self-Signed Certificate
Warning
If you installed Platform Manager with the default settings, HTTPS on SSL is already enabled.
To alter the Platform Manager integration with SSL
The following procedure applies if y'all are running multiple Information technology Service Management servers.
- In Cloud Portal and Database ITSM, open the CMF:PluginConfiguration form and change the Root URL from http to https and update the SSL port to 9443.
- In both ITSM hosts, import the RootCA certificate.
- Copy the RootCA.crt certificate to both hosts in its own folder (for case, C:\Certificates).
-
Import the document by entering post-obit command.
C:\Program Files\Java\jre7\bin>keytool -import -alias root -keystore "C:\Plan Files\Java\jre7\lib\security\cacerts" -trustcacerts -file C:\Certificates\RootCA.crt Enter keystore password: Owner: EMAILADDRESS=jstamps@bmc.com, CN=bmc.com, OU=IDD, O=BMC, L=San Jose, ST=C A, C=Us Issuer: EMAILADDRESS=jstamps@bmc.com, CN=bmc.com, OU=IDD, O=BMC, 50=San Jose, ST= CA, C=United states Serial number: 802aae2101b14487 Valid from: Thu Apr 10 13:52:46 PDT 2014 until: Fri Apr 10 13:52:46 PDT 2015 Certificate fingerprints: MD5: 15:4C:BE:02:B4:1D:6D:05:12:78:62:fourteen:41:A5:AD:DA SHA1: DE:B4:DF:5D:4E:58:B2:0B:EB:37:D7:57:F9:71:13:6B:CE:A5:05:B9 SHA256: A5:AC:79:D0:E3:21:BA:88:E7:78:77:CD:E8:18:88:14:96:CC:64:64:FD: D6:12:76:CE:BF:70:BB:28:82:30:D9 Signature algorithm name: SHA1withRSA Version: three Extensions: #1: ObjectId: ii.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: 33 28 60 0A C6 83 xvi 47 D9 E2 4A D7 6B F9 DC 76 3(`....G..J.m..v 0010: 0D 6C 58 51 .lXQ ] ] #2: ObjectId: 2.v.29.35 Criticality=faux AuthorityKeyIdentifier [ KeyIdentifier [ 0000: 33 28 60 0A C6 83 16 47 D9 E2 4A D7 6B F9 DC 76 three(`....Grand..J.chiliad..v 0010: 0D 6C 58 51 .lXQ ] ] #three: ObjectId: 2.five.29.19 Criticality=simulated BasicConstraints:[ CA:true PathLen:2147483647 ] Trust this certificate? [no]: aye Certificate was added to keystore
You do not need to import RootCA into the C:\ProgramFile\Java\Jre\bin path.
-
Restart the Platform Manager and AR System servers.
- Verify your changes by putting the RESTClient on the ITSM host and connecting to the Platform Manager host with SSL URL and thetrustcacerts path of Cloud Java (every bit above).
To configure BMC Chapters Optimization with SSL
Alarm
If you installed BMC Capacity Optimization with HTTPS on SSL, these instructions do not apply to you lot. Do not complete these steps if SSL is already enabled on the host. Otherwise, you run the chance of accidentally breaking functionality that is already working properly.
This is a two-step process:
- Generating a certificate and key to apply with Apache
- Enabling Apache to utilise HTTPS for BMC Capacity Optimization
To generate a certificate and key to utilize with Apache
-
Install the following packages on the host if they are not already present.
-
crypto-utils
-
mod_ssl
-
-
Subsequently installing these packages, generate a new key and a new SSL document using the genkey $hostname command.
Here $hostname is the fully qualified domain proper noun of your BMC Capacity Optimization awarding server machine. -
To create a certificate request, select the appropriate option.
Enter the certificate fields with your information (Name, Firm, State, and so on). If you do not want to manually insert a password every time yous restart the Apache Httpd server (forexample, if yous are in an automatic HA environment), clear the encrypt cardinal option.
-
During fundamental generation, review the post-obit output on the console:
[root@clm-bco ~]# genkey csm-bco /usr/bin/keyutil -c genreq -g 2048 -s "CN=csm-bco, OU=CDL, O=BMC, L=PUN, ST=MAHA, C=IN" -v 24 -a -o /etc/pki/tls/certs/csm-bco.0.csr -yard /etc/pki/tls/private/csm-bco.key -z /etc/pki/tls/.rand.24660 cmdstr: genreq cmd_CertReq command: genreq keysize = 2048 $.25 subject area = CN=csm-bco, OU=CDL, O=BMC, Fifty=PUN, ST=MAHA, C=IN valid for 24 months output will exist written to /etc/pki/tls/certs/csm-bco.0.csr output cardinal written to /etc/pki/tls/private/csm-bco.key random seed from /etc/pki/tls/.rand.24660 Generating key. This may take a few moments... Made a cardinal Opened /etc/pki/tls/certs/csm-bco.0.csr for writing Wrote the CSR to /etc/pki/tls/certs/csm-bco.0.csr Wrote 882 bytes of encoded data to /etc/pki/tls/private/csm-bco.key Wrote the primal to: /etc/pki/tls/private/csm-bco.primal /usr/bin/keyutil -c makecert -grand 2048 -south "CN=csm-bco, OU=CDL, O=BMC, 50=PUN, ST=MAHA, C=IN" -v 1 -a -z /etc/pki/tls/.rand.24660 -o /etc/pki/tls/certs/csm-bco.crt -k /etc/pki/tls/private/csm-bco.key cmdstr: makecert cmd_CreateNewCert control: makecert keysize = 2048 bits subject = CN=csm-bco, OU=CDL, O=BMC, L=PUN, ST=MAHA, C=IN valid for 1 months random seed from /etc/pki/tls/.rand.24660 output will be written to /etc/pki/tls/certs/csm-bco.crt output key written to /etc/pki/tls/private/csm-bco.keyTheCertificate Signing Request (csm-bco.0.csr) file is generated at the /etc/pki/tls/certs location.
-
Copy the csm-bco-0.csr file where you take CA or generate the CA certificate.
Or send this csr file to CA to get certificate. -
On the OpenSSL host, generate the certifcate, using the csm-bco-0.csr file.
C:\OpenSSL-Win64\bin>openssl x509 -req -days 365 -in C:\CSR\csm-bco.0.csr -CA C:\Certificates\RootCA.crt -CAkey C:\Keys\RootCA.key -set_serial 878 -out C:\Certificates\csm-bco.crt Loading 'screen' into random state - washed Signature ok subject=/C=IN/ST=MAHA/L=PUN/O=BMC/OU=CDL/CN=csm-bco Getting CA Individual Central -
When you finish generating the key, you have the following results:
- $hostname.crt document file in /etc/pki/tls/certs/
- $hostname.key central file in /etc/pki/tls/individual/
- Create /pki/tls/certs and /pki/tls/private folders at $CPITBASE/3rd_party/apache2/etc.
- Copy /etc/pki/tls/certs/ $hostname.crt to $CPITBASE/3rd_party/apache2/etc/pki/tls/certs/<hostname>.cert.
- Re-create /etc/pki/tls/private/ $hostname.cardinal to $CPITBASE/3rd_party/apache2/etc/pki/tls/ private/<hostname>.key.
- Alter the owner of both the copied files and the created folders to the possessor using BMC Capacity Optimization.
To enable HTTPS in Apache
Notation
- Make sure that the ssl.conf file is present under $CPITBASE/3rd_party/apache2/etc/httpd/conf.d. If not, then create it with post-obit SSL contents.
- Make sure that the mod_ssl.so file is present under $CPITBASE/3rd_party/apache2/etc/httpd/modules. If not, and so copy it from the /etc/httpd/modules path.
To enable HTTPS in your BMC Capacity Optimization installation, perform the post-obit steps:
-
Change the caplan.conf configuration file located at $CPITBASE/3rd_party/apache2/etc/httpd/conf.d, by adding the following information:
SSLEngine on SSLProxyEngine on SSLProtocol all -SSLv2 SSLCipherSuite ALL:!ADH:!Consign:!SSLv2:RC4+RSA:+Loftier:+MEDIUM:+LOW SSLCertificateFile $CPITBASE/3rd_party/apache2/etc/pki/tls/certs/<hostname>.crt SSLCertificateKeyFile $CPITBASE/3rd_party/apache2 /etc/pki/tls/individual/<hostname>.key -
Create the ssl.conf file in $CPITBASE/3rd_party/apache2/etc/httpd/conf.d and add the following content.
LoadModule ssl_module modules/mod_ssl.and then Mind 8443 AddType application/10-x509-ca-cert .crt AddType application/x-pkcs7-crl .crl SSLPassPhraseDialog builtin SSLSessionCache shmcb:/var/cache/mod_ssl/scache(512000) SSLSessionCacheTimeout 300 SSLMutex default SSLRandomSeed startup file:/dev/urandom 256 SSLRandomSeed connect builtin SSLCryptoDevice builtin
Brand sure that you change the required SSL port. - Restart Httpd using the $CPITBASE/cpit restart httpd command.
The new URL to connect to BCO will be https://$hostname:8443/console. -
Import the document into /gfs/cpit/jre/lib/security/cacerts for the trusted CA certificate.
[root@clm-bco bin]# ./keytool -import -alias root -keystore /gfs/cpit/jre/lib/security/cacerts -trustcacerts -file /etc/pki/tls/certs/RootCA.crt Enter keystore countersign: Owner: EMAILADDRESS=clm.bmc.com, CN=CLM, OU=CDL, O=BMC, L=PUN, ST=MAHA, C=IN Issuer: EMAILADDRESS=clm.bmc.com, CN=CLM, OU=CDL, O=BMC, L=PUN, ST=MAHA, C=IN Serial number: bfae9d478d3085c1 Valid from: Fri Apr 26 xiv:32:23 IST 2013 until: Sat Apr 26 14:32:23 IST 2014 Document fingerprints: MD5: E7:87:3D:B3:33:82:9F:17:0B:F6:78:D1:0D:64:EB:F5 SHA1: 47:85:B7:4E:46:C4:8F:21:31:29:86:47:C5:7A:3C:7F:65:B6:36:27 Signature algorithm name: SHA1withRSA Version: 1 Trust this certificate? [no]: aye Certificate was added to keystore - When you access the BCO URL, review the following certificate:
To integrate BMC Capacity Optimization and Platform Manager changes into SSL
Annotation
If y'all are integrating BMC Capacity Optimization with HTTPS mode with PM, you practise not need to perform any transmission steps. The integration itself take care of all the required steps.
To configure BMC Atrium Orchestrator with SSL
A HA environment typically has the following components installed.
- Host A Chief: AMREPO (Access Director and Repository) and CDP installed
- Host B Secondary: AMREPO and HACDP installed
- Host C: SQL DB for AMREPO
In non-HA environments,BMC Atrium Orchestrator Admission Manager and Repository are installedon a single server. For example, see To install Atrium Orchestrator AMREPO in Installing Pocket-sized Deployment Windows for version 4.7.
- On the main AO hosts (for example, Host A and B), create Keys , Certificates , and CSR folders.
-
Stop the Access Manager and Repository service and the Configuration Distribution Peer (CDP) service.
- Open up a command prompt and navigate to the AMREPOJRE folder (for example, C:\Program Files\BMC Software\AO-Platform\AMREPO\jvm\bin).
-
On master Host A, create a keypair using the keytool utility.
If Atrium Orchestrator is backside a load balancer, utilize CN as the load balancer name.
At the prompts, enter the required information to create the keypair, and then printingEnter.keytool.exe -genkey -alias AO -keyalg RSA -keysize 2048 -keypass "changeit" -storepass "changeit" -keystore C:\Keys\keystore.jks What is your start and last name? [Unknown]: vw-aus-clmidd04.bmc.com What is the proper name of your organizational unit of measurement? [Unknown]: IDD What is the name of your organization? [Unknown]: BMC Software What is the name of your City or Locality? [Unknown]: SAN JOSE What is the name of your State or Province? [Unknown]: California What is the two-letter country code for this unit of measurement? [Unknown]: United states of america Is CN=vw-aus-clmidd04.bmc.com, OU=IDD, O=BMC, L=SAN JOSE, ST=California, C=Us correct? [no]: aye -
Create the Certificate Signing Request (ao.csr) from AO primary to retrieve the document from CA (i.e. CLM).
At the prompt, enterchangeitequally the countersign.
keytool.exe -certreq -keyalg RSA -alias AO -file C:\CSR\ao.csr -keystore C:\Keys\keystore.jks Enter keystore countersign: -
Copy theao.csr file to theCSR folder where OpenSSL is installed so that you can generate a certificate, then run the following control on the OpenSSL computer:
C:\OpenSSL-Win64\bin>openssl x509 -req -days 365 -in "C:\CSR\ao.csr" -CA "C:\Certificates\RootCA.crt" -CAkey "C:\Keys\RootCA.key" -set_serial 999 -out "C:\Certificates\ao.crt" Loading 'screen' into random state - done Signature ok subject=/C=US/ST=California/Fifty=SAN JOSE/O=BMC Software/OU=IDD/CN=vw-aus-clmidd04.bmc.com Getting CA Private Primal -
After the certificate is generated (ao.crt) in theCertificates folder, copyao.crt andRootCA.crt and paste them to the AO chief and AO secondary into theirCertificates folder.
To configure AMREPO to work with SSL
-
On the AO primary and AO secondary hosts, import the Root CA certificate.
At the prompt, enter changeit as the password. When you lot see theTrust this certificate prompt, enteryes. Your document is added to the keystore.keytool.exe -import -alias root -keystore C:\Keys\keystore.jks -trustcacerts -file C:\Certificates\RootCA.crt Enter keystore password: Owner: EMAILADDRESS=jstamps@bmc.com, CN=vw-aus-clmidd05.bmc.com, OU=IDD, O=BMC Software, Fifty=San Jose, ST=California, C=Us ... Trust this certificate? [no]: yeah Certificate was added to keystore -
Import the ao.crt certificate into the AO JVM security folder.
At the prompt, enter changeit as the countersign.
Your document respond is installed in the keystore.keytool.exe -import -allonym root -keystore "C:\Plan Files\BMC Software\AO-Platform\AMREPO\ jvm\jre\lib\security\cacerts" -trustcacerts -file C:\Certificates\RootCA.crt Enter keystore password: Owner: EMAILADDRESS=jstamps@bmc.com, CN=vw-aus-clmidd05.bmc.com, OU=IDD, O=BMC Software, 50=San Jose, ST=California, C=United states ... Trust this certificate? [no]: yes Document was added to keystore -
Import the ao.crt certificate into keystore.jks (for example, C:\Keys\keystore.jks):
keytool.exe -import -allonym AO -keystore C:\Keys\keystore.jks -trustcacerts -file C:\Certificates\ao.crt Enter keystore password: Document reply was installed in keystore -
Open the Access Manager server.xml file (in Windows, for example,C:\Plan Files\BMC Software\AO-Platform\AMREPO\tomcat\conf\server.xml) in a text editor and uncomment the SSL related sections.
-
Search for the following text and uncomment out the
Connector portsection:
<!-- Define a SSL HTTP/one.one Connector on port 8443 This connector uses the JSSE configuration, when using APR, the connector should be using the OpenSSL mode configuration described in the April documentation --> <!-- <Connector port="8443" protocol="HTTP/1.1" SSLEnabled="truthful" maxThreads="150" scheme="https" secure="true" clientAuth="false" sslProtocol="TLS" /> --> -
Modifythe
Connector portinformation equally follows.
Uncomment the post-obit section and alter the protocol from HTTP/1.1 toorg.apache.coyote.http11.Http11Protocol, and add the keystoreFile path for keystore.jks.
Brand sure that you relieve the file.
Note
This section likewise includes the ciphers that fix theweak imperceptible Diffie-Hellman key error that you see with Google Chrome browsers.
<Connector port="8443" protocol="org.apache.coyote.http11.Http11Protocol" SSLEnabled="true" maxThreads="150" scheme="https" secure="true" clientAuth="faux" sslProtocol="TLS" ciphers="TLS_RSA_WITH_AES_128_CBC_SHA256, TLS_RSA_WITH_AES_256_CBC_SHA256, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P384, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P521, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P256, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P521, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P256, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P384, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P521, TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384_P384, TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384_P521, TLS_RSA_WITH_NULL_SHA256, TLS_RSA_WITH_AES_128_CBC_SHA, SSL_RSA_WITH_3DES_EDE_CBC_SHA" keystoreFile="C:\Keys\keystore.jks" />
-
-
Update the Login page entry in the context.xml file (for example, C:\Program Files\BMC Software\AO-Platform\AMREPO\tomcat\conf\context.xml) as follows:
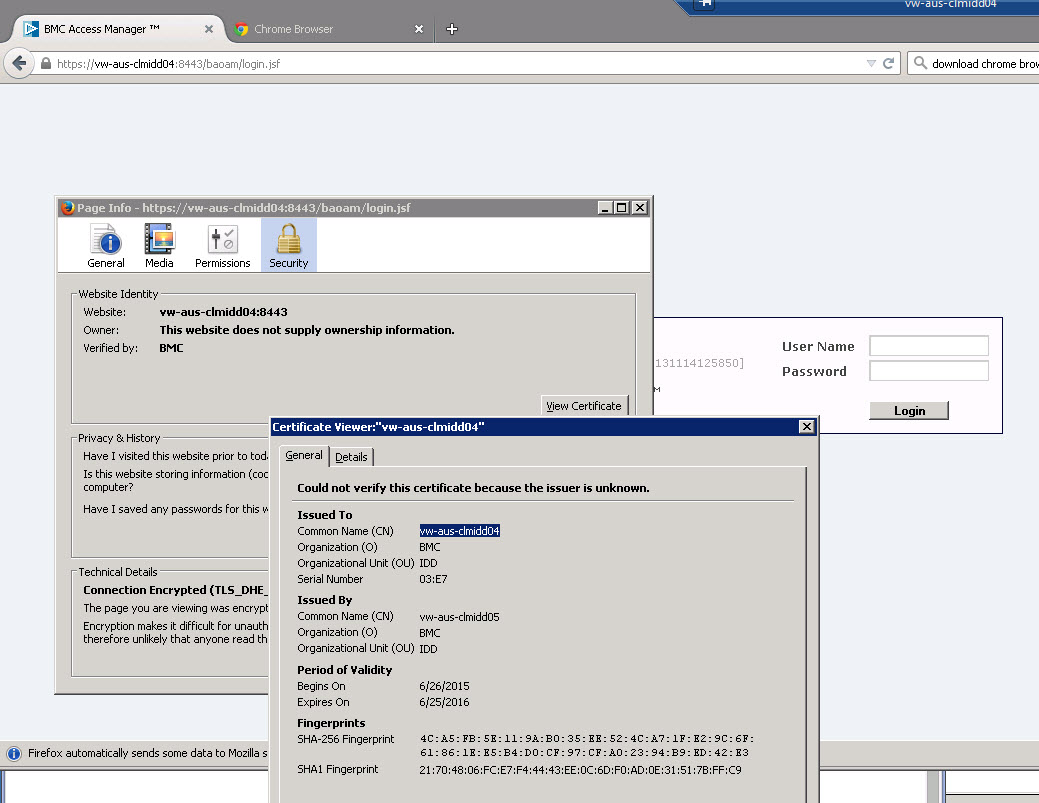
<Environment name="com.bmc.security.am.LOGIN_PAGE" override="truthful" type="java.lang.String" value="https://clm-hou-007778:8443/baoam/login.jsf"/> - Start the AMREPO server and verify the Access Manager URL.
For example:
https://AMPrimaryHost:8443/baoam
- Add and confirm any security restrictions in your browser.
For instance, the certificate should display Issued by: bmc.com and Issued to: vw-aus-clmidd04.
- Verify the Repository Manager URL and certificates.
For example:
https://AMPrimaryHost:8443/baorepo
- Brand the aforementioned changes to the secondary AMREPO server.
- Copy the keystore file.
- Update the server.xml and context.xml files.
- Import the Root CA certificate.
- Start the secondary Access Managing director server.
- Verify the URL.
To configure principal and secondary CDP to work with SSL
Note
For CDP, utilise the same RootCA.crt and keystore.jks files you previously generated. In improver, use the keystore.jks file from the C:\Keys\keystore.jks path.
-
Modify the server.xml file (for case,C:\Programme Files\BMC Software\AO-Platform\CDP\tomcat\conf\ server.xml ) every bit follows.
Uncomment the following section and update the required port (for example, 9443 ), change the protocol from HTTP/1.i to org.apache.coyote.http11.Http11Protocol ,and add together the keystoreFile path for keystore .
Notation
This section also includes the ciphers that fix theweak ephemeral Diffie-Hellman key error that you see with Google Chrome browsers.
<Connector port="9443" protocol="org.apache.coyote.http11.Http11Protocol" SSLEnabled="true" maxThreads="150" scheme="https" secure="true" clientAuth="false" sslProtocol="TLS" ciphers="TLS_RSA_WITH_AES_128_CBC_SHA256, TLS_RSA_WITH_AES_256_CBC_SHA256, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P384, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P521, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P256, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P521, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P256, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P384, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P521, TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384_P384, TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384_P521, TLS_RSA_WITH_NULL_SHA256, TLS_RSA_WITH_AES_128_CBC_SHA, SSL_RSA_WITH_3DES_EDE_CBC_SHA" keystoreFile="C:\Keys\keystore.jks" /> -
Modify the context.xml file (for instance,C:\Program Files\BMC Software\AO\AM\CDP\ tomcat\conf\context.xml) in a text editor.
Update the post-obit entry withhttps.
<Parameter proper name="com.bmc.ao.REPOSITORY_URL" override="true" value="https://vw-aus-clmidd04:9443/baorepo/http"/> -
Change directories to the primary CDP JRE/bin folder, for case, C:\Program Files\BMC Software\AO-Platform\CDP\jvm\jre\bin.
-
Import the ROOTCA .crt document into the primary CDP JVM security folder.
At the prompt, enterchangeitas the countersign.
Your certificate answer is installed in the keystore.
keytool.exe -import -alias root -keystore "C:\Program Files\BMC Software\AO-Platform\CDP\ jvm\jre\lib\security\cacerts" -trustcacerts -file C:\certificates\RootCA.crt Enter keystore password: Owner: EMAILADDRESS=jstamps@bmc.com, CN=JOHN, OU=IDD, O=BMC, L=SJ, ST=CA, C=United states Issuer: EMAILADDRESS=jstamps@bmc.com, CN=JOHN, OU=IDD, O=BMC, L=SJ, ST=CA, C=The states ... Trust this certificate? [no]: yes Document was added to keystore - Import theROOTCA .crt document into the secondary CDP JVM security binder.
-
On the secondary CDP host, modify thecontext.xml file (for case,C:\Program Files\BMC Software\AO\AM\CDP\ tomcat\conf\context.xml) in a text editor.
Update the post-obit entries with corrected port and https.
Parameter proper noun="com.bmc.ao.HACDP_CONFIGURATION" override="true" value="https://admin:admin123@vw-hou-sln-qa18:9443/ baocdp/ws/install?grid=GRID1&peer=HACDP"/> <Environs name="grid-name" override="true" type="java.lang.String" value="GRID1"/> <Environment name="peer-endpoint-urls" override="true" type="java.lang.String" value="https://vw-hou-sln-qa18:9443/ baocdp/ws/panel"/> - Start the CDP server on both nodes and verify the URL.
For case:
https://<CDPHost>:9443/baocdp
- Add and confirm any security restrictions in your browser.
The certificate should displayIssued by: bmc.com andIssued to: vw-aus-clmidd04. -
Admission theBMC Server Automation application server from Atrium Orchestrator hosts,
When you access the BMC Server Automation application server from Atrium Orchestrator hosts, it should display the following certificate details.
To configure BMC Server Automation and Atrium Orchestrator with SSL
You already generated the keystore.jks file in C:\Keys\keystore.jks and theRootCA.crt file in C:\Certificates on both hosts.
-
Import the RootCA.crt document into the Bladelogic coffee security file on both nodes equally follows:
keytool.exe -import -alias root -keystore "C:\Program Files\BMC Software\BladeLogic\NSH\jre\ lib\security\cacerts" -trustcacerts -file C:\Certificates\RootCA.crt - Log into the BMC Server Automation server from both hosts with defaultProfile and verify the certificate obtained.
To configure Atrium Orchestrator and Platform Manager with SSL
-
On the Platform Manager server, update the provider.json file for AO details similar https and ports number wherever required.
For instance:[{ "cloudClass" : "com.bmc.cloud.model.beans.Provider", "accessValues" : [ { "cloudClass" : "com.bmc.cloud.model.beans.AccessAttributeValue", "accessAttribute" : { "cloudClass" : "com.bmc.cloud.model.beans.AccessAttribute", "datatype" : "Cord", "guid" : "52461ff1-2ec4-11e0-91fa-0800200c9a66", "isOptional" : faux, "isPassword" : faux, "modifiableWithoutRestart" : false, "proper noun" : "AO_SERVER_URL" }, "attributeValue" : "https://clm-hou-007778:9443/baocdp/orca", "guid" : "78274c00-9d52-4b7a-bd07-7e7bfa413855", "name" : "AO_SERVER_URL" } - Restart Platform Manager.
To configure Atrium Orchestrator and ITSM with SSL
- On the Cloud Portal and Database server, open the CMF PluginConfiguration grade and update Atrium Orchestrator details like FIELD_AO_PROTOCOL, the FIELD_AO_PORT, and so on.
- Restart the AR System server.
To configure Cloud Portal Spider web Application from HTTP to HTTPS with a Self-Signed Certificate
Warning
If you installed Cloud Portal Web Application with the default settings, HTTPS on SSL is already enabled. Do non complete these steps if SSL is already enabled on the host. Otherwise, you run the risk of accidentally breaking functionality that is already working properly.
Apply the post-obit steps to configure HTTP to HTTPS using a Self-Signed Certificate.
-
Generate a certificate.
For example:
keytool -genkey -allonym tomcat -keyalg RSA -keystore "C:\clmuiSslCertificate.cert" -dname "cn=vw-sjc-sln-qa32,ou=CLM,o=BMC,50=PUN,southward=MH,c=IN" -keypass "changeit" -storepass "changeit" -validity 36500 - Copy the certificate to the required location.
For example:
C:\Program Files\BMC Software\CloudPortalWebApplication\clmui\Certificates\clmuiSslCertificate.cert - Update C:\Program Files\BMC Software\CloudPortalWebApplication\tomcat\conf\server.xml.
-
Replace the Connector entry:
<Connector connectionTimeout="20000" port="9070" protocol="HTTP/ane.1" redirectPort="9443"/> -
With the following information:
<Connector SSLEnabled="true" clientAuth="false" connectionTimeout="20000" keystoreFile="C:\Plan Files\BMC Software\CloudPortalWebApplication\ clmui\Certificates\clmuiSslCertificate.cert" keystorePass="changeit" maxThreads="150" port="9443" scheme="https" secure="true" sslProtocol="TLS"/>
-
- RestartCloud Portal Web Application service.
To configure Cloud Portal Web Application from HTTPS to HTTP with a Self-Signed Certificate
Use the following steps to configure HTTPS to HTTP using a Self-Signed Certificate.
- UpdateC:\Program Files\BMC Software\CloudPortalWebApplication\tomcat\conf\server.xml.
-
Supersede the Connector entry:
<Connector SSLEnabled="true" clientAuth="simulated" connectionTimeout="20000" keystoreFile="C:\Programme Files\BMC Software\ CloudPortalWebApplication\clmui\Certificates\clmuiSslCertificate.cert" keystorePass="changeit" maxThreads="150" port="9443" scheme="https" secure="truthful" sslProtocol="TLS"/> -
With the post-obit information:
<Connector connectionTimeout="20000" port="9070" protocol="HTTP/1.1" redirectPort="9443"/>
-
- Restart Cloud Portal Web Application service.
To configure CLM Self-Checker from HTTP to HTTPS with a Self-Signed Certificate
Warning
If you installed CLM Self-Checker with the default settings, HTTPS on SSL is already enabled. Practice non complete these steps if SSL is already enabled on the host. Otherwise, you run the gamble of accidentally breaking functionality that is already working properly.
Employ the post-obit steps to configure HTTP to HTTPS using a Cocky-Signed Certificate.
-
Generate a certificate.
For example:
C:\Program Files\Java\jre1.7.0_55\bin>keytool -genkey -alias tomcat -keyalg RSA -keystore "C:\ selfcheckerSslCertificate.cert" -dname "cn=vw-sjc-sln-qa32,ou=CLM,o=BMC,fifty=PUN,due south=MH,c=IN" -keypass "changeit" -storepass "changeit" -validity 36500 - Copy the document to the required location.
For example:
C:\Plan Files\BMC Software\SelfChecker\selfchecker\Certificates\selfcheckerSslCertificate.cert - UpdateC:\Program Files\BMC Software\SelfChecker\tomcat\conf\server.xml .
-
Replace the Connector entry:
<Connector connectionTimeout="20000" port="8090" protocol="HTTP/one.1" redirectPort="8443"/> -
With the post-obit information:
<Connector SSLEnabled="true" clientAuth="false" connectionTimeout="20000" keystoreFile=" C:\Program Files\BMC Software\SelfChecker\selfchecker\ Certificates\selfcheckerSslCertificate.cert" keystorePass="changeit" maxThreads="150" port="8443" scheme="https" secure="true" sslProtocol="TLS"/>
-
-
Restartthe Self Checker service.
To configure CLM Self-Checker from HTTPS to HTTP with a Cocky-Signed Document
Use the following steps to configure HTTPS to HTTP using a Self-Signed Certificate.
- UpdateC:\Program Files\BMC Software\SelfChecker\tomcat\conf\server.xml.
-
Supersede the Connector entry:
<Connector SSLEnabled="true" clientAuth="false" connectionTimeout="20000" keystoreFile="C:\Program Files\BMC Software\SelfChecker\ selfchecker\Certificates\selfcheckerSslCertificate.cert" keystorePass="changeit" maxThreads="150" port="8443" scheme="https" secure="true" sslProtocol="TLS"/> -
With the following information:
<Connector connectionTimeout="20000" port="8090" protocol="HTTP/1.1" redirectPort="8443"/>
-
- Restart the Self Checker service.
To configure BMC MyIT from HTTP to HTTPS with a Self-Signed Certificate
Warning
Do not complete these steps if SSL is already enabled with BMC MyIT. Otherwise, you run the risk of accidentally breaking functionality that is already working properly.
-
Generate a document.
For example:
%JAVA_HOME%\bin\keytool -genkey -alias tomcat -keyalg RSA Enter keystore password: Re-enter new password: What is your starting time and last proper name? [Unknown]: clm-aus-011540,bmc.com What is the name of your organizational unit? [Unknown]: IDD What is the name of your arrangement? [Unknown]: BMC Software What is the proper noun of your City or Locality? [Unknown]: San Jose What is the name of your State or Province? [Unknown]: California What is the two-alphabetic character country code for this unit? [Unknown]: Us Is CN="clm-aus-011540,bmc.com", OU=IDD, O=BMC Software, L=San Jose, ST=Californi a, C=U.s.a. correct? [no]: yeah Enter cardinal password for <tomcat> (RETURN if same as keystore countersign):A .keystore file is generated in %USERPROFILE% (Windows) or $HOME (Linux), and the file is protected with a password.
- Place the generated file in the CATALINA_BASE/external-conf folder (for instance,C:\Program Files\Apache Software Foundation\Tomcat8.0\external-conf).
-
UpdateCATALINA_BASE/conf/server.xml to enable HTTPS Connector.
Note
This section besides includes the ciphers that set up theweak ephemeral Diffie-Hellman key error that yous see with Google Chrome browsers.
Uncomment the post-obit section , and update the section equally follows (for example, add together the keystoreFile path for keystore), and so on.<Connector port="8443" protocol="org.apache.coyote.http11.Http11NioProtocol" maxThreads="150" SSLEnabled="truthful" scheme="https" secure="true" clientAuth="imitation" sslProtocol="TLS" ciphers="TLS_RSA_WITH_AES_128_CBC_SHA, TLS_RSA_WITH_AES_256_CBC_SHA256, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P384, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P521, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P256, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P521, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P256, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P384, TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P521, TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384_P384, TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384_P521, TLS_RSA_WITH_NULL_SHA256, TLS_RSA_WITH_AES_128_CBC_SHA, SSL_RSA_WITH_3DES_EDE_CBC_SHA" keystoreFile="${catalina.base}/external-conf/.keystore" sslEnabledProtocols="TLSv1.2,TLSv1.ane,TLSv1,SSLv2Hello" -
Restart the Tomcat server (SmartIT/MyIT Application).
-
To check the configuration, openhttps://localhost:8443/ or https://localhost:8443/ux/myitapp in a browser.
Upon initial access, a warning about an non-trusted certificate appears (because this is a self-signed document, not generated by a trusted CA). -
ClickOK to continue.
Yous should successfully exist logged on to the MyIT application using SSL.
Using CLM applications with third-party Certification Authority certificates
Was this page helpful? Yes No Submitting... Thank you
Source: https://docs.bmc.com/docs/cloudlifecyclemanagement/46/enabling-ssl-on-windows-680302962.html
Posted by: millerbeftelf1970.blogspot.com











0 Response to "How To Enable Ssl In Windows 10"
Post a Comment